
Metasploitable 2 Linux – Most Vulnerable OS in the town : Introduction and Installation | Information Treasure
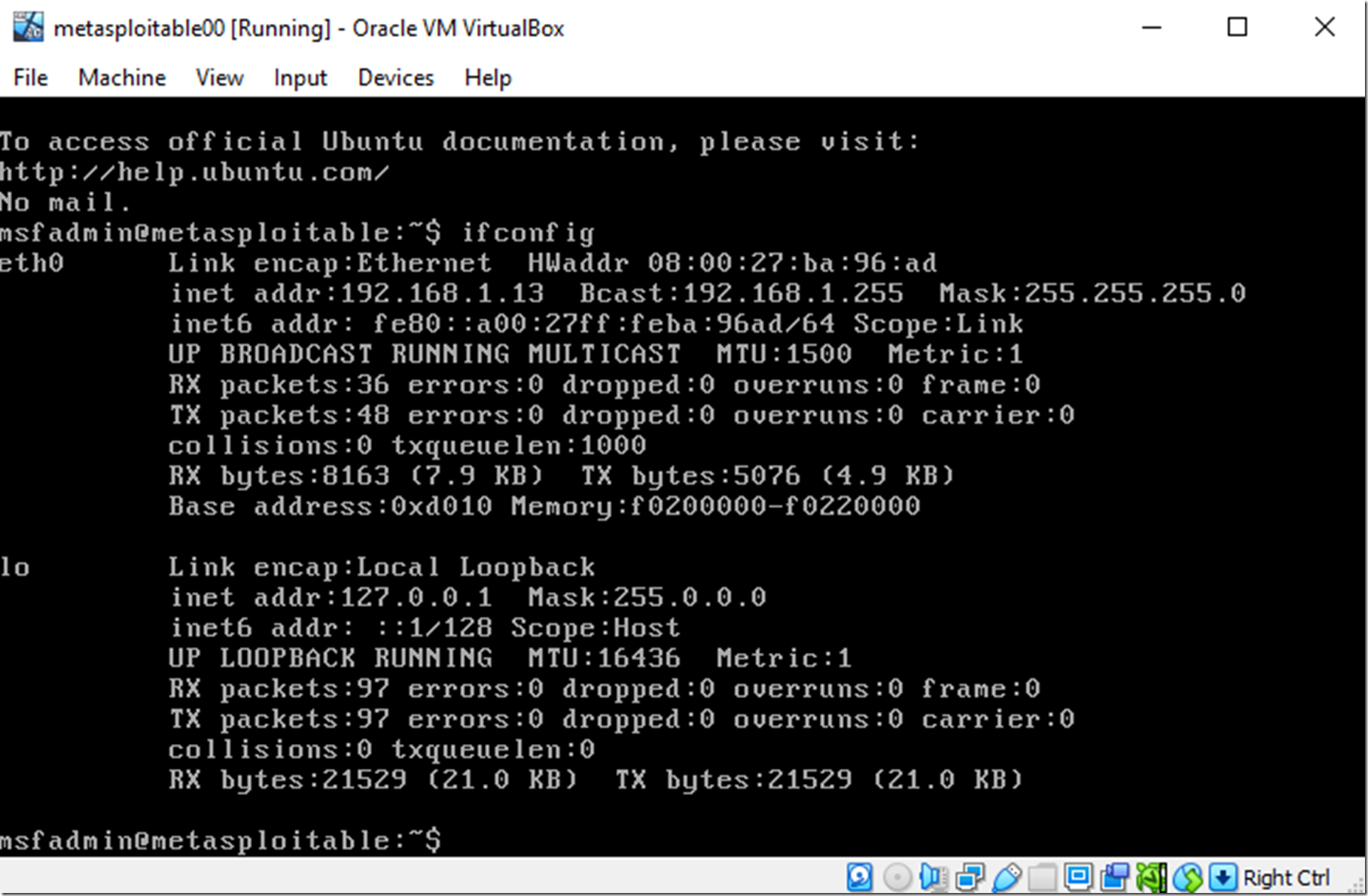
Setting up a hacking lab with Kali Linux and Metasploitable, Part 1 | The Best C# Programmer In The World - Benjamin Perkins
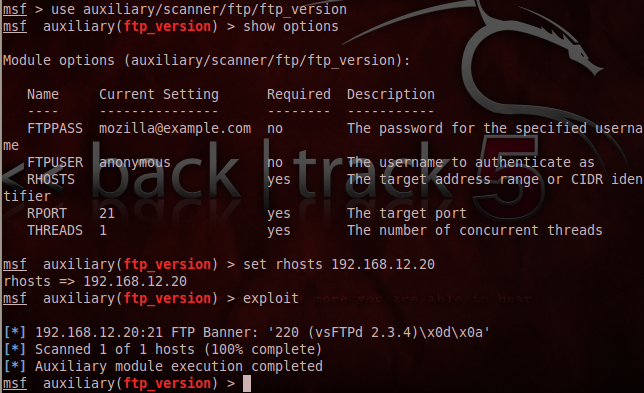
Metasploitable 2.0 Tutorial Part 2: Scanning for Network Services with Metasploit – CYBER ARMS – Computer Security
Setting up a hacking lab with Kali Linux and Metasploitable, Part 1 | The Best C# Programmer In The World - Benjamin Perkins
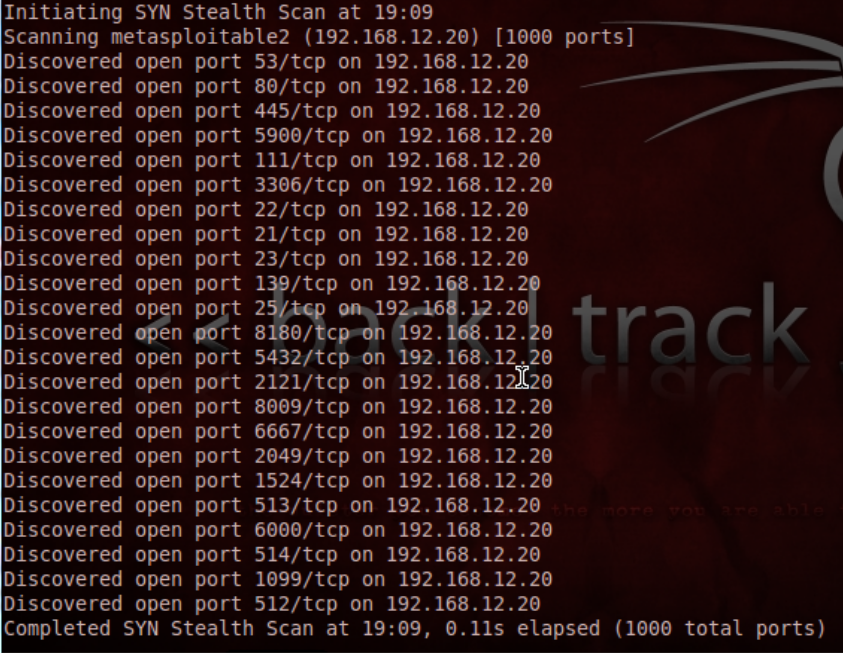
Metasploitable 2 Tutorial Part 1: Checking for open Ports with Nmap – CYBER ARMS – Computer Security

Metasploitable 2 Linux – Most Vulnerable OS in the town : Introduction and Installation | Information Treasure
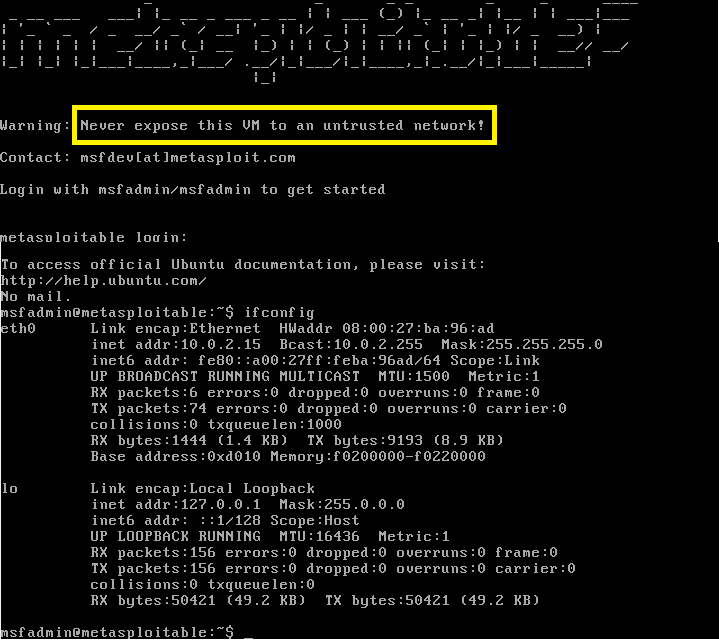
Setting up a hacking lab with Kali Linux and Metasploitable, Part 1 | The Best C# Programmer In The World - Benjamin Perkins

![Setup Hacking Lab with Metasploitable [7 Easy Steps] | GoLinuxCloud Setup Hacking Lab with Metasploitable [7 Easy Steps] | GoLinuxCloud](https://www.golinuxcloud.com/wp-content/uploads/meta-2.jpg)

![Setup Hacking Lab with Metasploitable [7 Easy Steps] | GoLinuxCloud Setup Hacking Lab with Metasploitable [7 Easy Steps] | GoLinuxCloud](https://www.golinuxcloud.com/wp-content/uploads/meta-4.jpg)
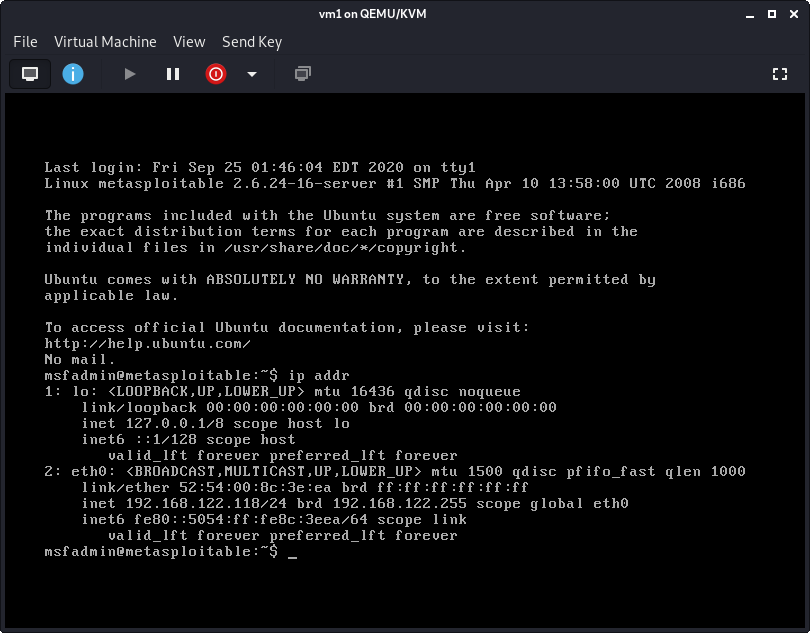



![Setup Hacking Lab with Metasploitable [7 Easy Steps] | GoLinuxCloud Setup Hacking Lab with Metasploitable [7 Easy Steps] | GoLinuxCloud](https://www.golinuxcloud.com/wp-content/uploads/meta-6.jpg)

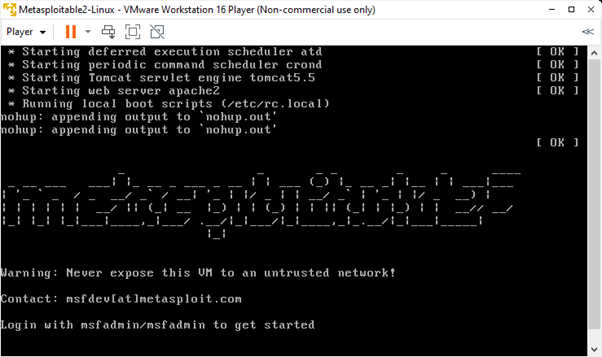
![Setup Hacking Lab with Metasploitable [7 Easy Steps] | GoLinuxCloud Setup Hacking Lab with Metasploitable [7 Easy Steps] | GoLinuxCloud](https://www.golinuxcloud.com/wp-content/uploads/meta-8.jpg)

